Key Management System Aws

Aws kms is a secure and resilient service that uses hardware security modules that have been validated under fips 140 2 or are in the process of being validated to.
Key management system aws. We then encrypt and decrypt the data using a data key that was generated by the aws cmk. In this section you can find information about ssh keys how to generate them and how to rotate them. Aws key management service aws kms is a managed service that makes it easy for you to create and control customer master keys cmks the encryption keys used to encrypt your data. Amazon elastic block store volumes amazon s3 objects using server side encryption sse kms and client side encryption using the.
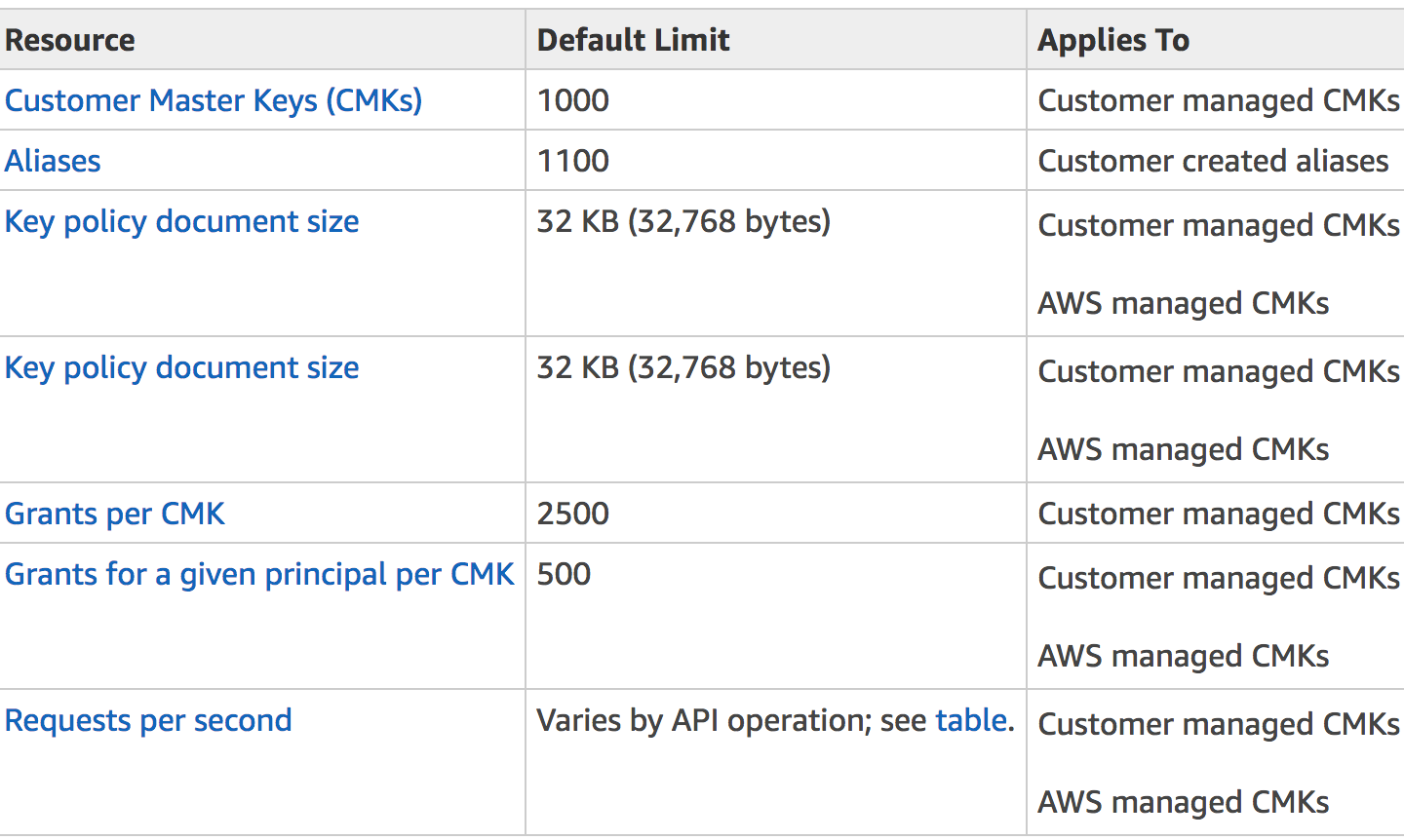
Aws kms cmks are protected by hardware security modules hsms that are validated by the fips 140 2 cryptographic module validation program except in the china beijing and china ningxia regions. On macos linux or unix operating systems open a command terminal. To perform a key rotation in the console. This feature allows you to select the appropriate key management configuration to meet your security and compliance requirements and meet the level of control required for.
Linux or unix operating system. We first encrypt and decrypt data directly using an aws customer managed key cmk. In this tutorial we explore the aws key management system kms to encrypt and decrypt data via the aws java 2 sdk. You can generate use rotate and destroy aes256 rsa 2048 rsa 3072 rsa 4096 ec p256 and ec p384 cryptographic keys.
Key management concerns keys at the user level either between users or systems. Aws key management service kms is now available in the aws govcloud us region. You can now encrypt data in your own applications and within the following aws services in govcloud by using keys under your control. Aws key management service kms makes it easy for you to create and manage cryptographic keys and control their use across a wide range of aws services and in your applications.
It includes cryptographic protocol design key servers user procedures and other relevant protocols. This tutorial encrypts decrypts two different ways.